Niagara Networks
Niagara Networks provides high-performance network visibility solutions to allow seamless administration of security solutions, performance management, and network monitoring. Niagara Networks products provide advantages in terms of network operation expenses, downtime, and total cost of ownership.
A former division of Interface Masters, Niagara Networks provides all the building blocks for an advanced Visibility Adaptation Layer at all data rates up to 100Gb, including Taps, bypass elements, packet brokers and a unified management layer. Thanks to its integrated in-house capabilities and tailor-made development cycle, Niagara Networks are agile in responding to market trends and in meeting the customized needs of service providers, enterprise, data centers, and government agencies.

Niagara Networks provides all the building blocks for an advanced Visibility Adaptation Layer at all data rates up to 100Gb, including taps, bypass elements, packet brokers and a unified management layer. Thanks to its integrated in-house capabilities and tailor-made development cycle, Niagara Networks are agile in responding to market trends and in meeting the customized needs of service providers, enterprise, data centers, and government agencies.
Network Packet Brokers
What is a Network Packet Broker
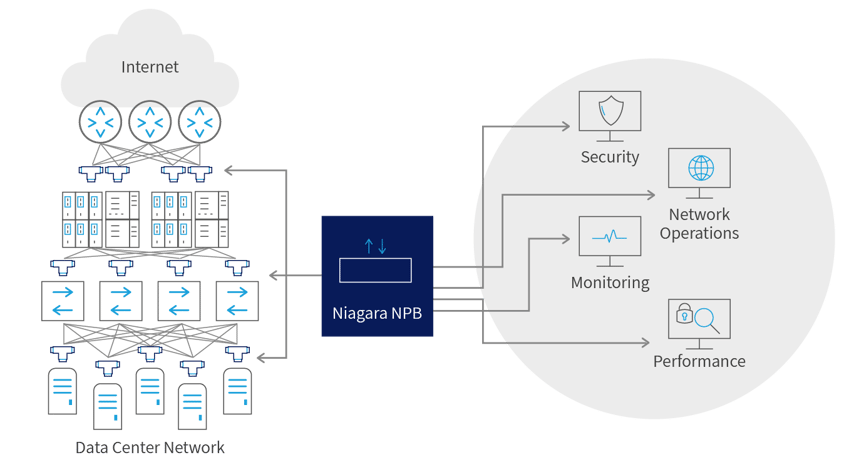
A Network Packet Broker (NPB) is an active device that directs selected raw data packets from network interfaces (typically via SPAN or tap points) to specific network service and monitoring devices, and performance management and security applications.
What Exactly Does a Network Packet Broker Do
Niagara’s NPB solutions perform a range of crucial functionalities for all types of networks, even those with extremely complex architectures and that are resource intensive including:
- Total Network Visibility - Identifying known, suspicious, and unknown traffic passing through the network
- Network robustness - Ensuring data loss prevention and advanced filtering, as well as high availability, stripping, and other special purpose packet capabilities
- Network management - Not just knowing how to monitor network traffic, but also knowing what to do with each type of traffic: where to pass known (authorized) data types, and how to handle suspicious and unknown traffic
Why You Need a Network Packet Broker
In their role as data analyzers, Niagara’s Packet Brokers can also handle deduplication of redundant (duplicate) packets before they reach analysis or security tools within the network, that are passed along by multiple taps forwarding their data traffic. The NPBs will eliminate those duplicates and make sure network tools do not waste resources on handling redundant data.
Basic data packet manipulation schema includes one network link, to one tool (one-to-one), one network link to multiple tools (one-to-many), multiple network links to one tool (many-to-one) and multiple network links to multiple tools (many-to-many) – interlaced and load balanced into a network-wide fabric.
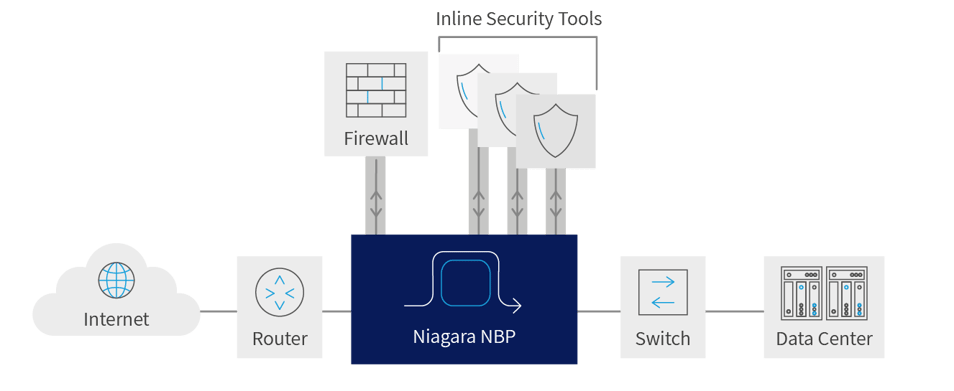
Bypass Switch
- Our Products:
- Network Packet Broker
Bypass Switch
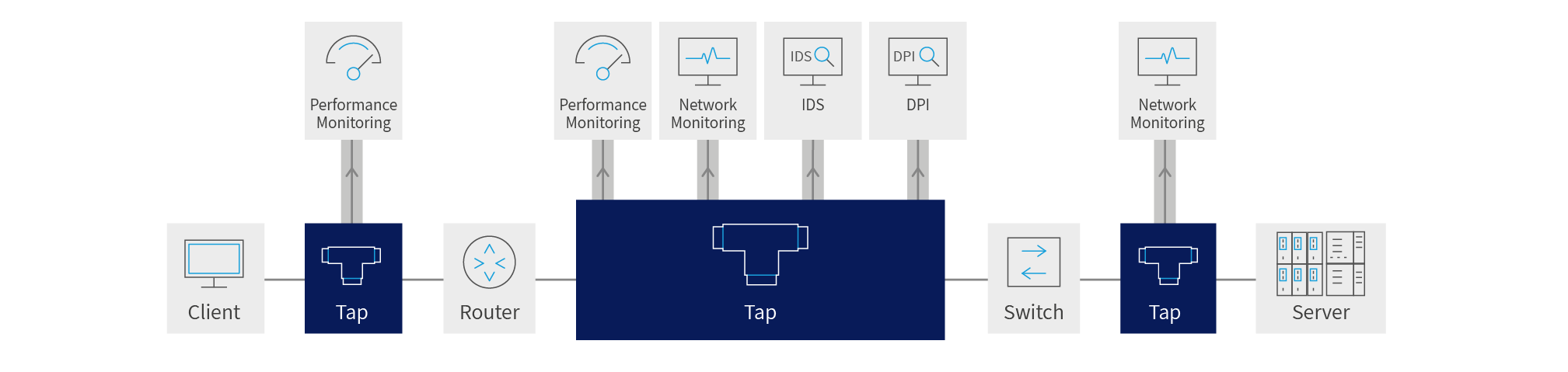
Network Taps